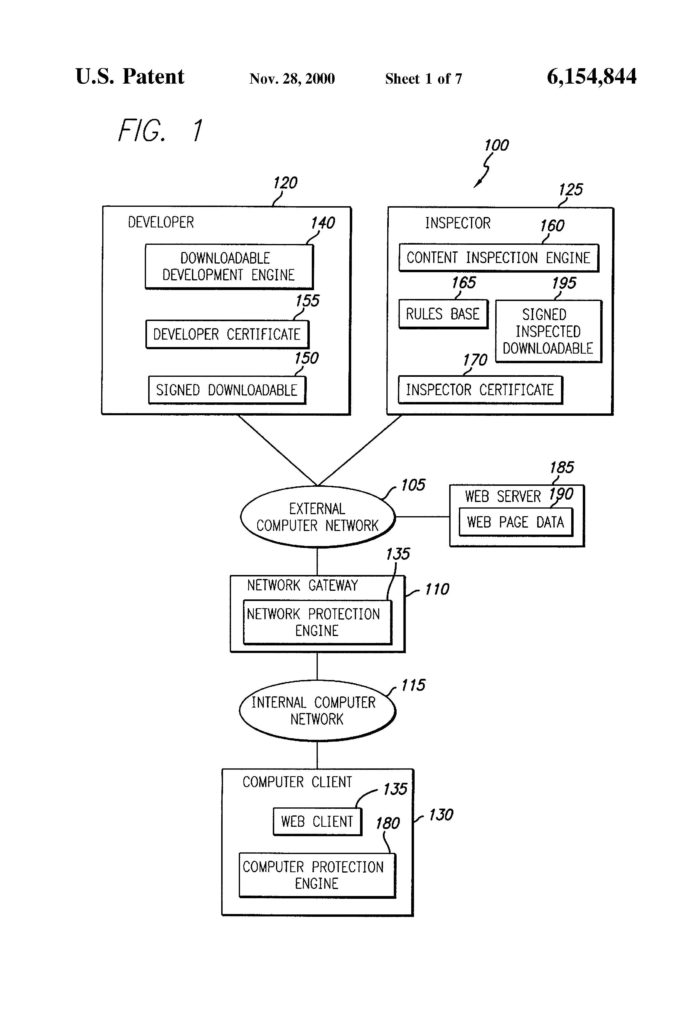
 Finjan brought suit against Blue Coat for infringement of software patents directed to identifying and protecting against malware. One of the software patents is directed to a method of providing computer security by scanning a downloadable and attaching the results of that scan to the downloadable itself in the form of a “security profile.”
Finjan brought suit against Blue Coat for infringement of software patents directed to identifying and protecting against malware. One of the software patents is directed to a method of providing computer security by scanning a downloadable and attaching the results of that scan to the downloadable itself in the form of a “security profile.”
Claim 1 of the patent reads:
1. A method comprising:
- receiving by an inspector a Downloadable;
- generating by the inspector a first Downloadable security profile that identifies suspicious code in the received Downloadable; and
- linking by the inspector the first Downloadable security profile to the Downloadable before a web server makes the Downloadable available to web clients.
The parties agreed that “Downloadable” should be construed to mean “an executable application program, which is downloaded from a source computer and run on the destination computer.” Additionally, the district court construed “Downloadable security profile that identifies suspicious code in the received Downloadable” to mean “a profile that identifies code in the received Downloadable that performs hostile or potentially hostile operations.”
The Federal Circuit noted that they had previously determined in Intellectual Ventures I LLC v. Symantec Corp. that, by itself, virus screening is well-known and constitutes an abstract idea. They also found that performing the virus scan on an intermediary computer—so as to ensure that files are scanned before they can reach a user’s computer— is a “perfectly conventional” approach and is also abstract. However, they felt that, here, the claimed method does a
good deal more.
The method of claim 1 scans a downloadable and attaches the virus scan results to the downloadable in the form of a newly generated file: a “security profile that identifies suspicious code in the received Downloadable.”
The district court’s claim construction decision emphasized that this “identify suspicious code” limitation can only be satisfied if the security profile includes “details about the suspicious code in the received downloadable, such as . . . ‘all potentially hostile or suspicious code operations that may be attempted by the Downloadable.’” The security profile must include the information about potentially hostile operations produced by a “behavior-based” virus scan. This operation is distinguished from traditional, “code-matching” virus scans that are limited to recognizing the presence of previously-identified viruses, typically by comparing the code in a downloadable to a database of known suspicious code. The question, then, is whether this behavior-based virus scan constitutes an improvement in computer functionality. The Federal Circuit believes that it does.
The “behavior-based” approach to virus scanning was pioneered by Finjan and is disclosed in the software patent’s specification. Traditional “code-matching” systems simply look for the presence of known viruses.
“Behavior-based” scans can analyze a downloadable’s code and determine whether it performs potentially dangerous or unwanted operations—such as renaming or deleting files. Because security profiles communicate the granular information about potentially suspicious code made available by behavior-based scans, they can be used to protect against previously unknown viruses as well as “obfuscated code”—known viruses that have been cosmetically modified to avoid detection by code-matching virus scans.
The security profile approach also enables more flexible and nuanced virus filtering. After an inspector generates a security profile for a downloadable, a user’s computer can determine whether to access that downloadable by reviewing its security profile according to the rules in whatever “security policy” is associated with the user. Administrators can easily tailor access by applying different security policies to different users or types of users. And having the security profile include information about particular potential threats enables administrators to craft security policies with highly granular rules and to alter those security policies in response to evolving threats.
The Federal Circuit’s cases confirm that software inventions can make “non-abstract improvements to computer technology” and be deemed patent-eligible subject matter at step 1 of the Alice software patent inquiry. In Enfish, for example, the Federal Circuit determined that claims related to a database architecture that used a new, self-referential logical table were non-abstract because they focused on “an improvement to computer functionality itself, not on economic or other tasks for which a computer is used in its ordinary capacity.”
The self referential database found patent eligible in Enfish did more than allow computers to perform familiar tasks with greater speed and efficiency; it actually permitted users to
launch and construct databases in a new way. While deployment of a traditional relational database involved extensive modeling and configuration of the various database, Enfish’s self-referential database could be launched with no or only minimal column definitions and configured and adapted “on-the-fly.”
Similarly, according to the Federal Circuit, the software patent method of claim 1 employs a new kind of file that enables a computer security system to do things it could not do before. The security profile approach allows access to be tailored for different users and ensures that threats are identified before a file reaches a user’s computer. The fact that the security profile identifies suspicious code allows the system to accumulate and utilize newly available, behavior-based information about potential threats. According to the Federal Circuit, the asserted claims are therefore directed to a non-abstract improvement in computer functionality, rather than the abstract idea of computer security at large.
Patent eligibility determinations seem to vary greatly based on the judges on the Federal Circuit panel hearing the case. In this case, the novelty of the method seemed to influence the patent-eligibility determination. If novelty is a main consideration, why even bother with the Alice 35 U.S.C. 101 analysis when reviewing software patents? While the claim was short, many claim terms were construed as requiring very specific steps. That may have helped with the patent-eligibility determination.
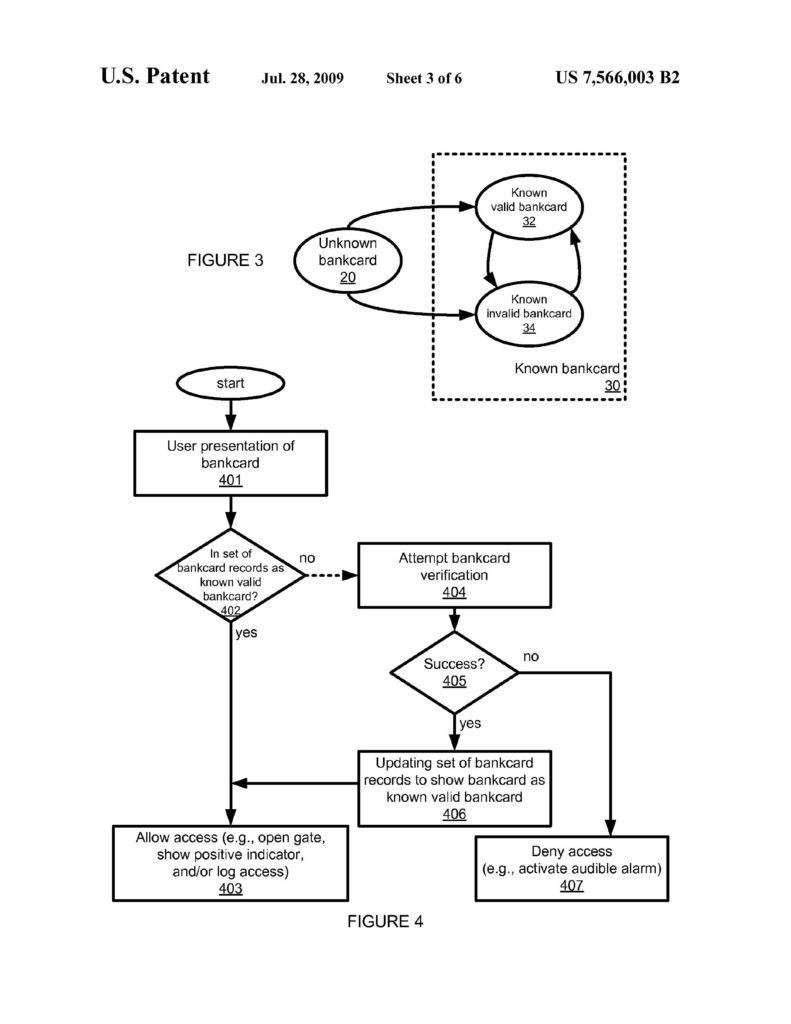 This case concerned an appeal from a district court case which held that Visual Memory’s U.S. Patent No. 5.953,740 was drawn to patent-ineligible subject matter.
This case concerned an appeal from a district court case which held that Visual Memory’s U.S. Patent No. 5.953,740 was drawn to patent-ineligible subject matter.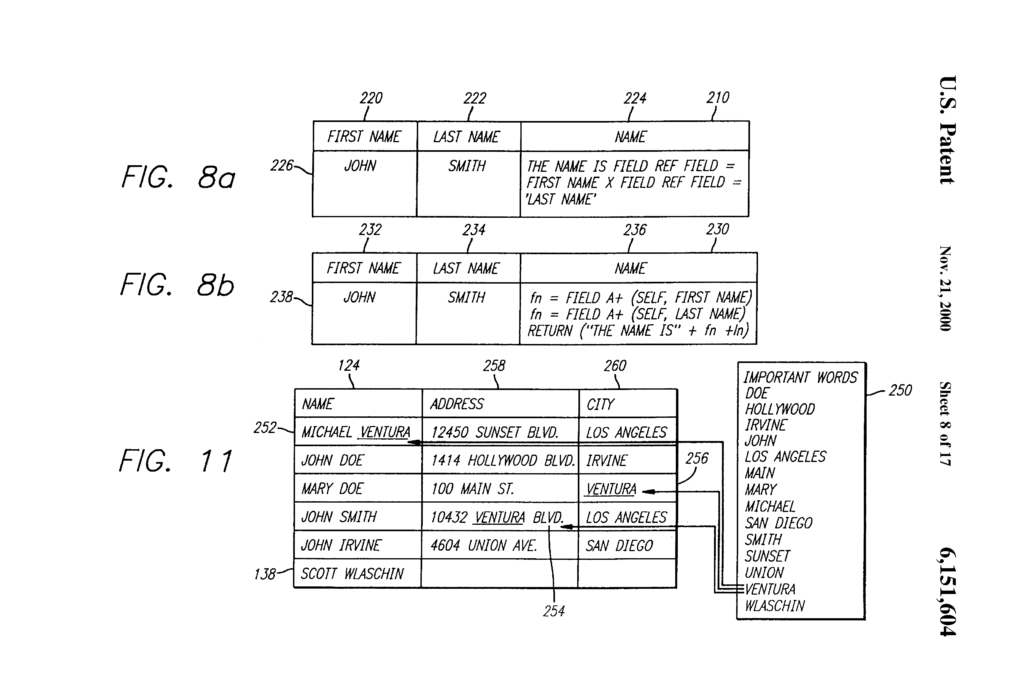 Enfish sued Microsoft for infringement of U.S. Patent 6,151,604 and U.S. Patent 6,163,775 related to a logical model for a computer database. A logical model is a model of data for a computer database explaining how the various elements of information are related to one another. A logical model generally results in the creation of particular tables of data, but it does not describe how the bits and bytes of those tables are arranged in physical memory devices. Contrary to conventional logical models, the patented logical model includes all data entities in a single table, with column definitions provided by rows in that same table. The patents describe this as a “self-referential” property of the database.
Enfish sued Microsoft for infringement of U.S. Patent 6,151,604 and U.S. Patent 6,163,775 related to a logical model for a computer database. A logical model is a model of data for a computer database explaining how the various elements of information are related to one another. A logical model generally results in the creation of particular tables of data, but it does not describe how the bits and bytes of those tables are arranged in physical memory devices. Contrary to conventional logical models, the patented logical model includes all data entities in a single table, with column definitions provided by rows in that same table. The patents describe this as a “self-referential” property of the database.