The Federal Circuit stated in this decision that CareDx’s patents apply conventional measurement techniques to detect a natural phenomenon—the level of donor cfDNA and the likelihood of organ transplant rejection.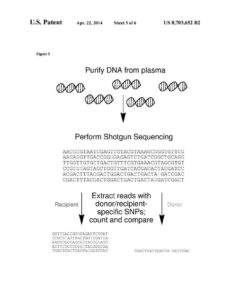
CareDx and Stanford appealed a decision holding that Stanford’s Patents 8,703,652, 9,845,497, and 10,329,607 are ineligible for patent under 35 U.S.C. § 101. The three patents share the same specification and are entitled “Non-Invasive Diagnosis of Graft Rejection in Organ Transplant Patients.” These patents discuss diagnosing or predicting organ transplant status by using methods to detect a donor’s cell-free DNA (“cfDNA”). When an organ
transplant is rejected, the recipient’s body, through its natural immune response, destroys the donor cells, thus releasing cfDNA from the donated organ’s dying cells into the blood. These increased levels of donor cfDNA—which occur naturally as the organ’s condition deteriorates—can be detected and then used to diagnose the likelihood of an organ
transplant rejection.
Claim 1 of the ’652 patent reads as follows:
1. A method for detecting transplant rejection, graft dysfunction, or organ failure, the method comprising:
- (a) providing a sample comprising [cfDNA] from a subject who has received a transplant from a donor;
- (b) obtaining a genotype of donor-specific polymorphisms or a genotype of subjectspecific polymorphisms, or obtaining both a genotype of donor-specific polymorphisms and subject-specific polymorphisms, to establish a polymorphism profile for detecting donor [cfDNA], wherein at least one single nucleotide polymorphism (SNP) is homozygous for the subject if the genotype comprises subject-specific polymorphisms comprising SNPs;
- (c) multiplex sequencing of the [cfDNA] in the sample followed by analysis of the sequencing results using the polymorphism profile to detect donor [cfDNA] and subject [cfDNA]; and
- (d) diagnosing, predicting, or monitoring a transplant status or outcome of the subject who has received the transplant by determining a quantity of the donor [cfDNA] based on the detection of the donor [cfDNA] and subject [cfDNA] by the multiplexed sequencing, wherein an increase in the quantity of the donor [cfDNA] over time is indicative of transplant rejection, graft dysfunction or organ failure, and wherein sensitivity of the method is greater than 56% compared to sensitivity of current surveillance methods for cardiac allograft vasculopathy (CAV).
The other patents are similar. In summary, the methods disclosed in the representative claims have four steps for detecting a donor’s cfDNA in a transplant recipient:
- 1. “obtaining” or “providing” a “sample” from the recipient that contains cfDNA;
- 2. “genotyping” the transplant donor and/or recipient
to develop “polymorphism” or “SNP” “profiles”; - 3. “sequencing” the cfDNA from the sample using
“multiplex” or “high-throughput” sequencing; or performing “digital PCR”; and - 4. “determining” or “quantifying” the amount of donor cfDNA.
CareDx argued that, regarding Alice/Mayo step one, the patents’ claimed advance is not the discovery of a natural correlation between organ rejection and the donor’s cfDNA levels in the recipient’s blood. Rather, the claimed
advance is improved measurement methods spelled out in the claims as superior to the inadequate prior art measurement techniques. CareDx also argued that the district court did not properly perform the step one analysis because it concluded that step one is essentially the same as step two and centers on conventionality. It asserted that there is no basis
in the law for a one-step application of Alice/Mayo.
Regarding Alice/Mayo step two, CareDx argued that using digital PCR and next-generation sequencing (“NGS”) to identify and measure donor-specific SNPs was an inventive breakthrough and that the patents claim this specific and useful application.
The Federal Circuit concluded that CareDx’s patents apply conventional measurement techniques to detect a natural phenomenon—the level of donor cfDNA and the likelihood of organ transplant rejection. They stated that the claimed methods are indistinguishable from other diagnostic method claims the Supreme Court found ineligible in Mayo and that we found ineligible on multiple occasions.
 Multilevel security claims were patent eligible because they were directed to solving a technical problem specific to computer network security. The district court correctly rejected Adobe’s ineligibility challenge.
Multilevel security claims were patent eligible because they were directed to solving a technical problem specific to computer network security. The district court correctly rejected Adobe’s ineligibility challenge.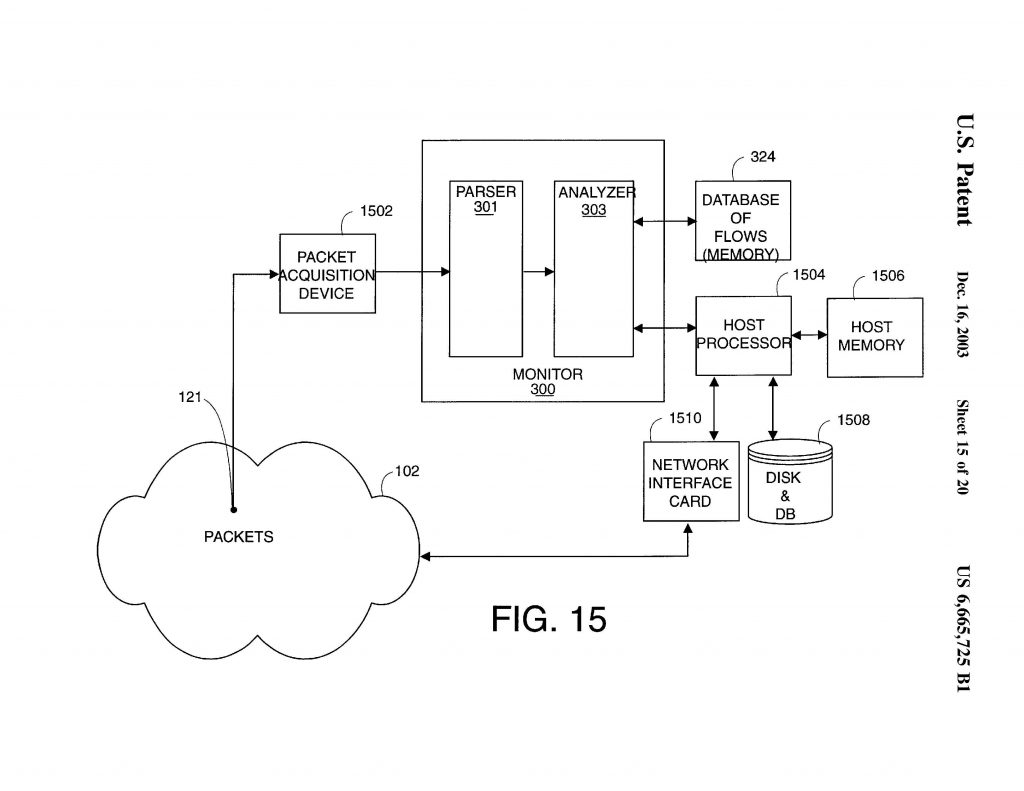 NetScout Systems appealed from a judgment of the U.S. District Court for the Eastern District of Texas which held that NetScout willfully infringed various claims of U.S. Patent No. 6,665,725; 6,839,751; and 6,954,789 and held that the claims were valid under 35 U.S.C. §101.
NetScout Systems appealed from a judgment of the U.S. District Court for the Eastern District of Texas which held that NetScout willfully infringed various claims of U.S. Patent No. 6,665,725; 6,839,751; and 6,954,789 and held that the claims were valid under 35 U.S.C. §101.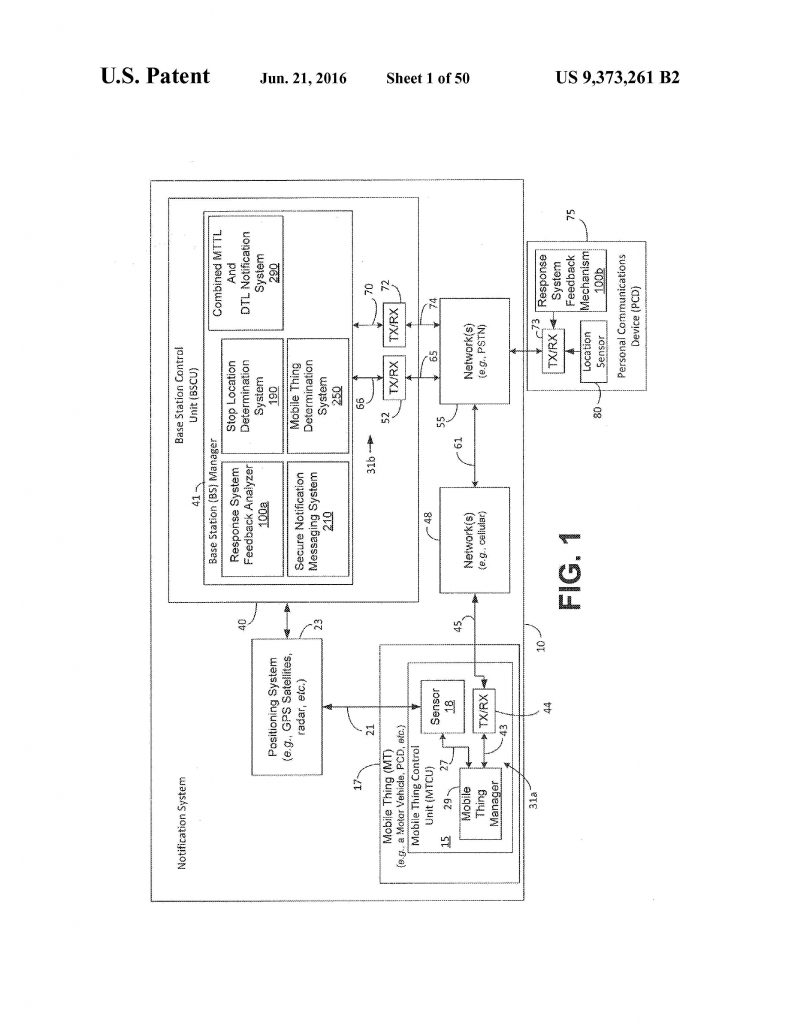 Electronic Communication Technologies, LLC sued ShoppersChoice.com, LLC (“ShoppersChoice”), alleging that ShoppersChoice infringed claim 11 of U.S. Patent No. 9,373,261. The district court granted ShoppersChoice’s motion for judgment on the pleadings that claim 11 was invalid under 35 U.S.C. § 101.
Electronic Communication Technologies, LLC sued ShoppersChoice.com, LLC (“ShoppersChoice”), alleging that ShoppersChoice infringed claim 11 of U.S. Patent No. 9,373,261. The district court granted ShoppersChoice’s motion for judgment on the pleadings that claim 11 was invalid under 35 U.S.C. § 101.