 NetScout Systems appealed from a judgment of the U.S. District Court for the Eastern District of Texas which held that NetScout willfully infringed various claims of U.S. Patent No. 6,665,725; 6,839,751; and 6,954,789 and held that the claims were valid under 35 U.S.C. §101.
NetScout Systems appealed from a judgment of the U.S. District Court for the Eastern District of Texas which held that NetScout willfully infringed various claims of U.S. Patent No. 6,665,725; 6,839,751; and 6,954,789 and held that the claims were valid under 35 U.S.C. §101.
The patents disclose a method for monitoring packets ex-changed over a computer network. A stream of packets between two computers is called a connection flow. Monitoring connection flows cannot account for disjointed sequences of the same flow in a network. The specifications explain that it is more useful to identify and classify “conversational flows,” defined as “the sequence of packets that are ex-changed in any direction as a result of an activity.” Conversational flows provide application-specific views of network traffic and can be used to generate helpful analytics to understand network load and usage.
Claim 19 of the ‘789 patent is representative and recites:
A packet monitor for examining packets passing through a connection point on a computer net-work, each packet conforming to one or more protocols, the monitor comprising:
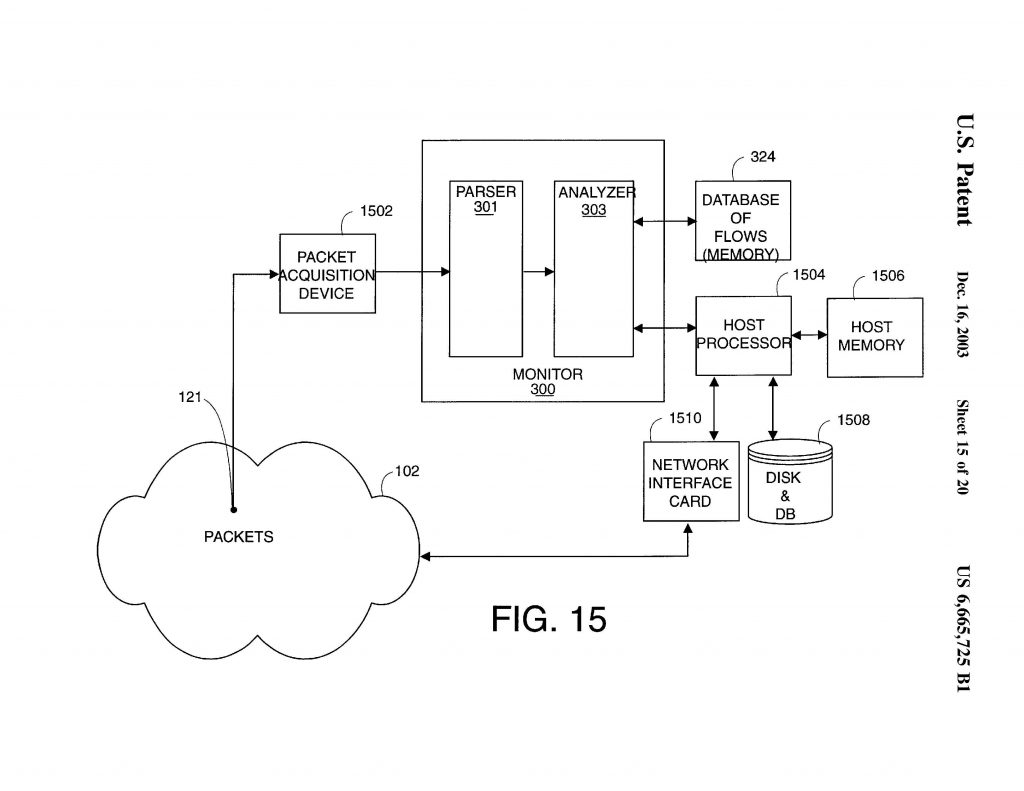
- (a) a packet acquisition device coupled to the connection point and configured to receive packets passing through the connection point;
- (b) an input buffer memory coupled to and configured to accept a packet from the packet acquisition device;
- (c) a parser subsystem coupled to the input buffer memory and including a slicer, the parsing subsystem configured to extract selected portions of the accepted packet and to output a parser record containing the selected portions;
- (d) a memory for storing a database comprising none or more flow-entries for previously encountered conversational flows, each flow-entry identified by identifying in-formation stored in the flow-entry;
- (e) a lookup engine coupled to the output of the parser subsystem and to the flow-entry memory and configured to lookup whether the particular packet whose parser record is output by the parser subsystem has a matching flow-entry, the looking up using at least some of the selected packet portions and determining if the packet is of an existing flow; and
- (f) a flow insertion engine coupled to the flow-entry memory and to the lookup engine and configured to create a flow-entry in the flow-entry database, the flow-entry including identifying information for future packets to be identified with the new flow-entry, the lookup engine configured such that if the packet is of an existing flow, the monitor classifies the packet as belonging to the found existing flow; and if the packet is of a new flow, the flow insertion engine stores a new flow-entry for the new flow in the flow-entry database, including identifying information for future packets to be identified with the new flow-entry,
- wherein the operation of the parser subsystem de-pends on one or more of the protocols to which the packet conforms.
NetScout claimed that the patents cover ineligible subject matter under 35 U.S.C. §101.
In evaluating patent eligibility, the Federal Circuit first determines whether the claims at issue are directed to a patent-ineligible concept in accordance with
Alice Corp. v. CLS Bank.
The district court first made a series of factual findings about the claimed inventions’ advantages over the prior art. According to the district court, to measure the amount or type of information being transmitted by a particular application or protocol, a network monitor must measure “all of the connection flows through which that application or protocol transmits packets.” The lower court found that prior art monitors could not identify disjointed connection flows as belonging to the same conversational flow. The patents addressed this “problem” in the art by parsing packets to extract information that can be used to associate packets with single conversational flows, which correspond to particular applications or protocols. The Alice analysis was thus really partly a novelty analysis.
With this factual background, the court applied the
Alice framework. First, the court rejected NetScout’s argument that claim 19 is directed to the collection, comparison, and classification of information. The court instead held that the claim was directed to “solving a discrete technical problem: relating disjointed connection flows to each other.” The court determined that the claim was directed to “specific technological solutions, such as identifying and refining a conversational flow so that different connection flows can be associated with each other and ultimately an underlying application or protocol.”
At step one, the district court also rejected NetScout’s argument that the claims are directed to an abstract idea because they do not explain how to determine whether packets belong to a conversational flow. According to the district court, NetScout’s argument focused on the claims in isolation instead of the claims as read in light of the specification.
Packet Intelligence faults NetScout for oversimplifying the claims and maintains that the district court was correct to consider the specification in its analysis.
The Federal Circuit agreed with Packet Intelligence that claim 19 is not directed to an abstract idea. In the eligibility analysis, the courts are to consider the claim as a whole, in view of
Diamond v. Diehr, and read it in light of the specification. The Federal Circuit has recognized that software-based innovations can make ‘non-abstract improvements to computer technology’ and be deemed patent-eligible subject matter at Alice step 1, as they did in
Finjan, Inc. v. Blue Coat Sys., Inc.According to the Federal Circuit, the asserted patents’ specifications make clear that the claimed invention presented a technological solution to a technological problem. The specifications explain that known network monitors were unable to identify disjointed connection flows to each other, and the focus of the claims is a specific improvement in computer technology: a more granular, nuanced, and useful classification of network traffic.
This was one of the few cases of 2020 in which “pure” software patents were held to be patent-eligible under 35 U.S.C. §101.
 NetScout Systems appealed from a judgment of the U.S. District Court for the Eastern District of Texas which held that NetScout willfully infringed various claims of U.S. Patent No. 6,665,725; 6,839,751; and 6,954,789 and held that the claims were valid under 35 U.S.C. §101.
NetScout Systems appealed from a judgment of the U.S. District Court for the Eastern District of Texas which held that NetScout willfully infringed various claims of U.S. Patent No. 6,665,725; 6,839,751; and 6,954,789 and held that the claims were valid under 35 U.S.C. §101.